║ ║
║ KHAN Games System Configuration (C) 1980-2025, Kevin Hanley, Inc., ║
║ Discord: khangames ║ ╠════════════════════════════════════════════════╦═════════════════════════════════════════════════════╣
║ Main Processor : 486DX2-S ║ Base Memory Size : 640 KB ║
║ Numeric Processor : Present ║ Ext. Memory Size : 261120 KB ║
║ Floppy Drive A: : 2.88 MB 3½" ║ Hard Disk C: Type : 47 ║
║ Floppy Drive B: : 1.2 MB 5¼" ║ Hard Disk D: Type : None ║
║ Display Type : VGA/EGA ║ Serial Port(s) : 3F8,2F8 ║
║ AMIBIOS Date : 12/15/93 ║ Parallel Port(s) : 378,278 ║
╚════════════════════════════════════════════════╩══════════════════════════════════╦══════════════════╣
║ Home · Guestbook ║
╚══════════════════╝
June 18, 2025
In an effort to step up our cybersecurity strength my colleagues and I decided to implement a pretty severe password strength requirement for in-office computers.
The upside is obviously tighter security with less likelyhood that someone off the street could somehow find their way into one of our offices and look on the wall and see a football team and decide to pair that with a year and plop into someone's Windows account. The downside was that we, the IT department, wouldn't have a master password list anymore for the times we needed to hop on there remotely and fix something (almost always a printer).
We were trying to figure out how we would be able to remote in "as the user" without knowing the passwords and we stumbled upon something called Shadow RDP. I'm sure most of you "in the field" are well aware of this, but it was new and exciting for us. The only issue is that
1: it's completely command line based and
2: the "port" that a user's PC is on is seeminly random, so while it's usually 1, it's not always 1.
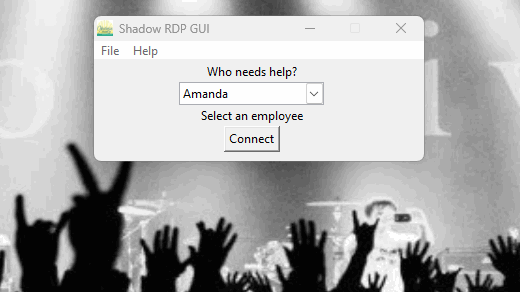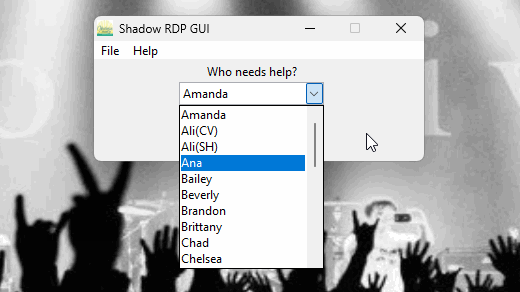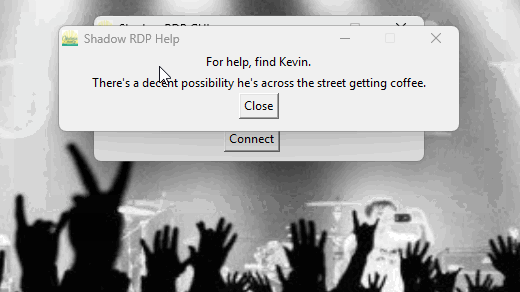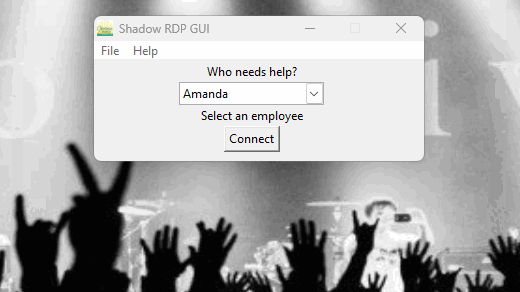
I knew there had to be a better way, so I put my smooth brain to use and coded a GUI in Python that looks up what port the PC is on and then automatically RDP's into their respective IP address. It's really helping us out.
The upside is obviously tighter security with less likelyhood that someone off the street could somehow find their way into one of our offices and look on the wall and see a football team and decide to pair that with a year and plop into someone's Windows account. The downside was that we, the IT department, wouldn't have a master password list anymore for the times we needed to hop on there remotely and fix something (almost always a printer).
We were trying to figure out how we would be able to remote in "as the user" without knowing the passwords and we stumbled upon something called Shadow RDP. I'm sure most of you "in the field" are well aware of this, but it was new and exciting for us. The only issue is that
1: it's completely command line based and
2: the "port" that a user's PC is on is seeminly random, so while it's usually 1, it's not always 1.
I knew there had to be a better way, so I put my smooth brain to use and coded a GUI in Python that looks up what port the PC is on and then automatically RDP's into their respective IP address. It's really helping us out.
June 17, 2025
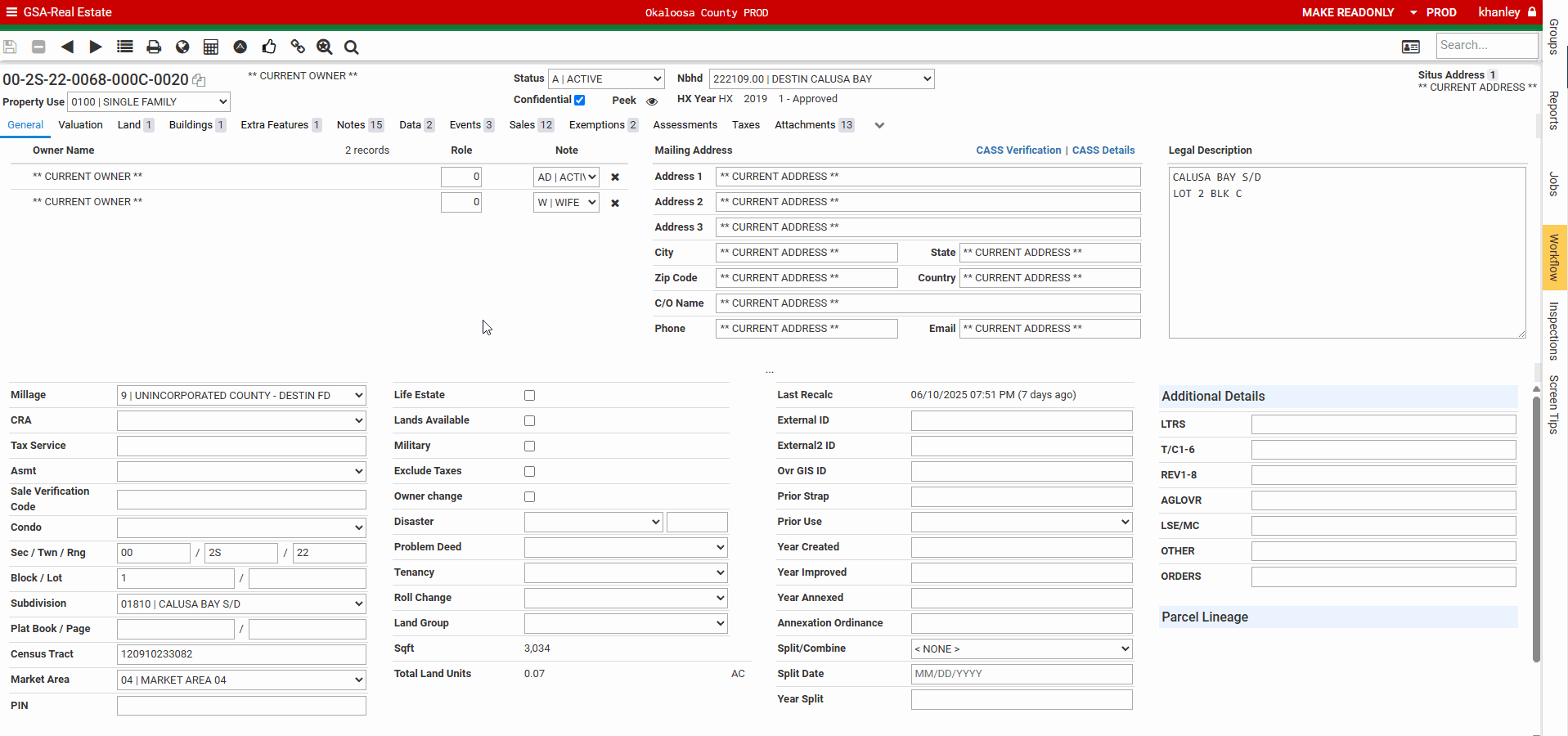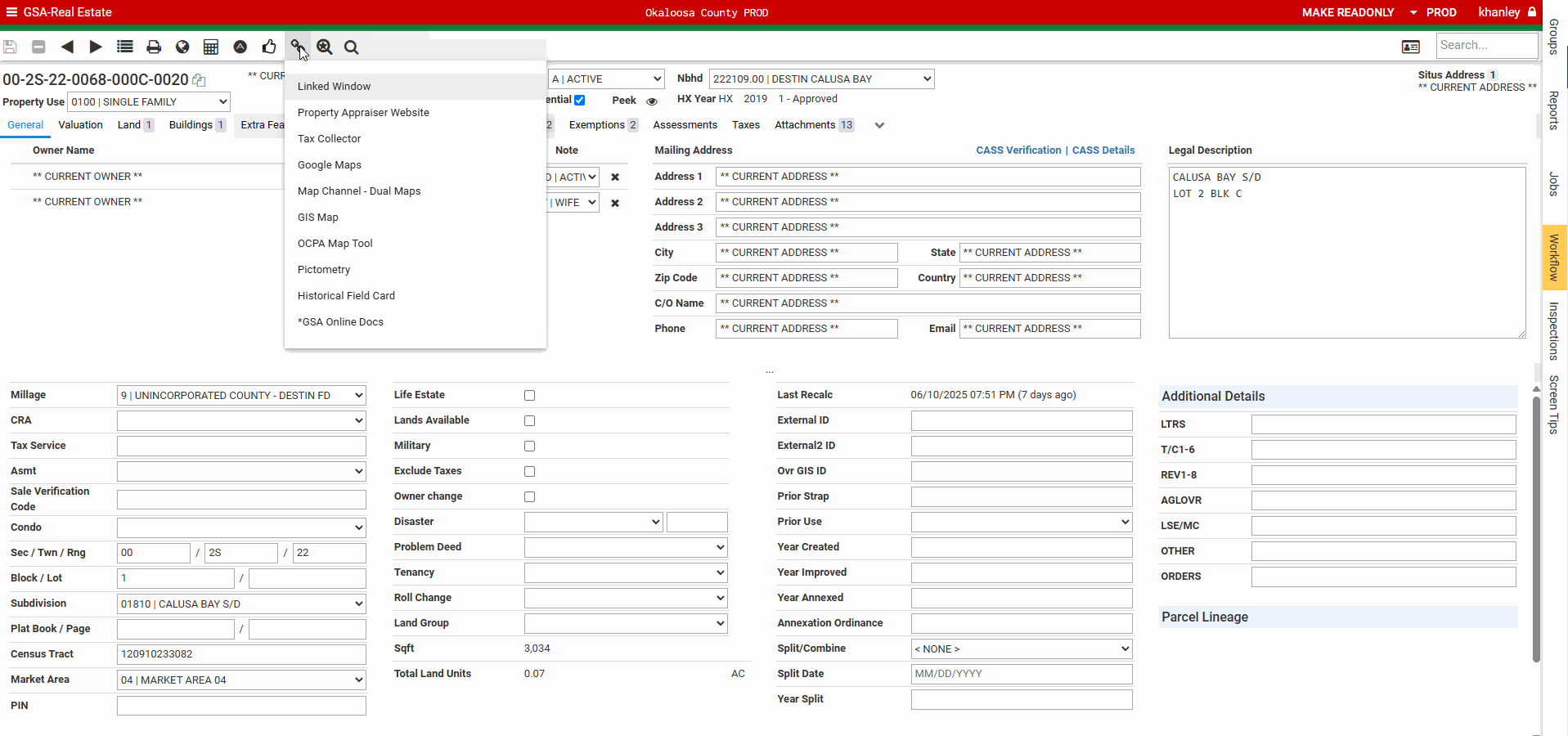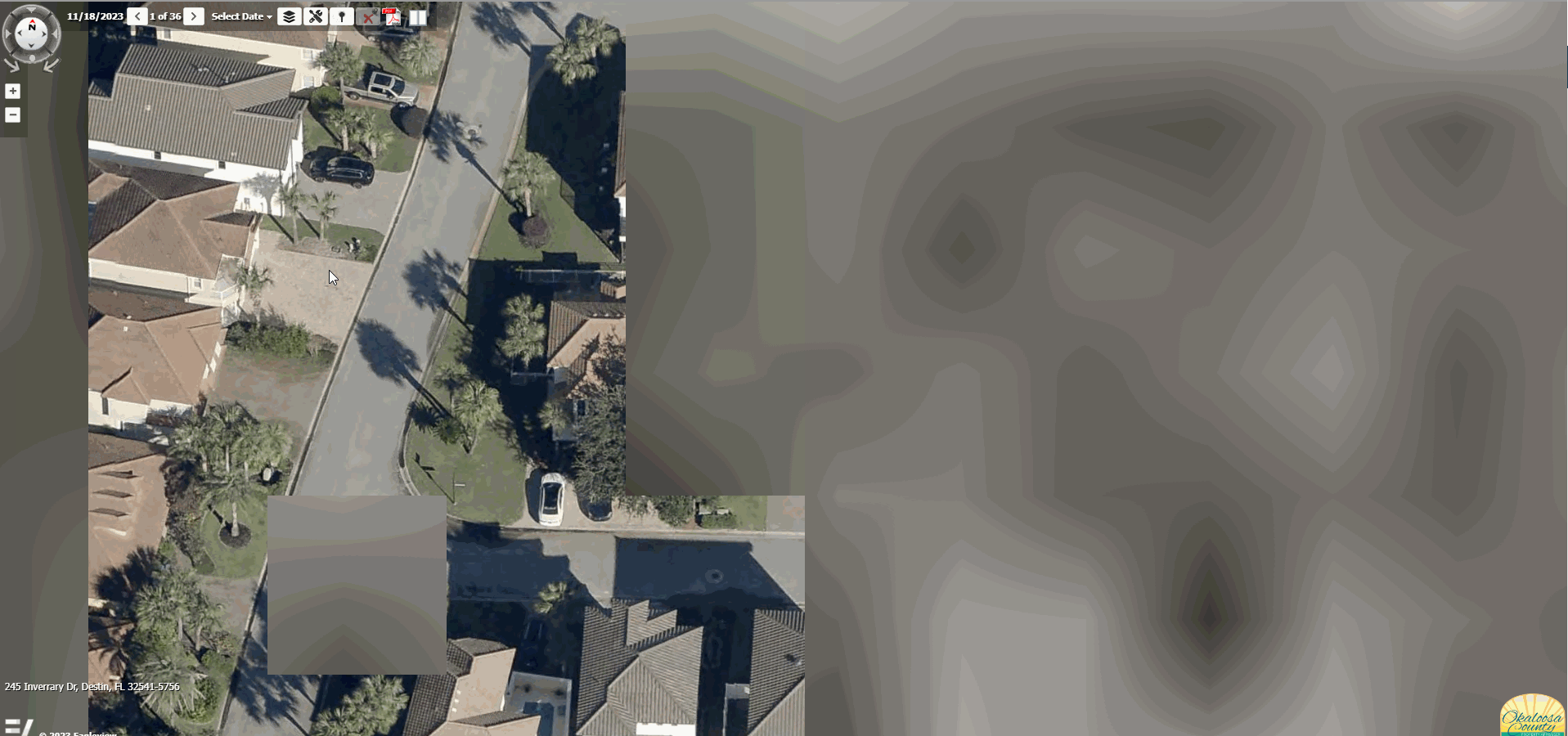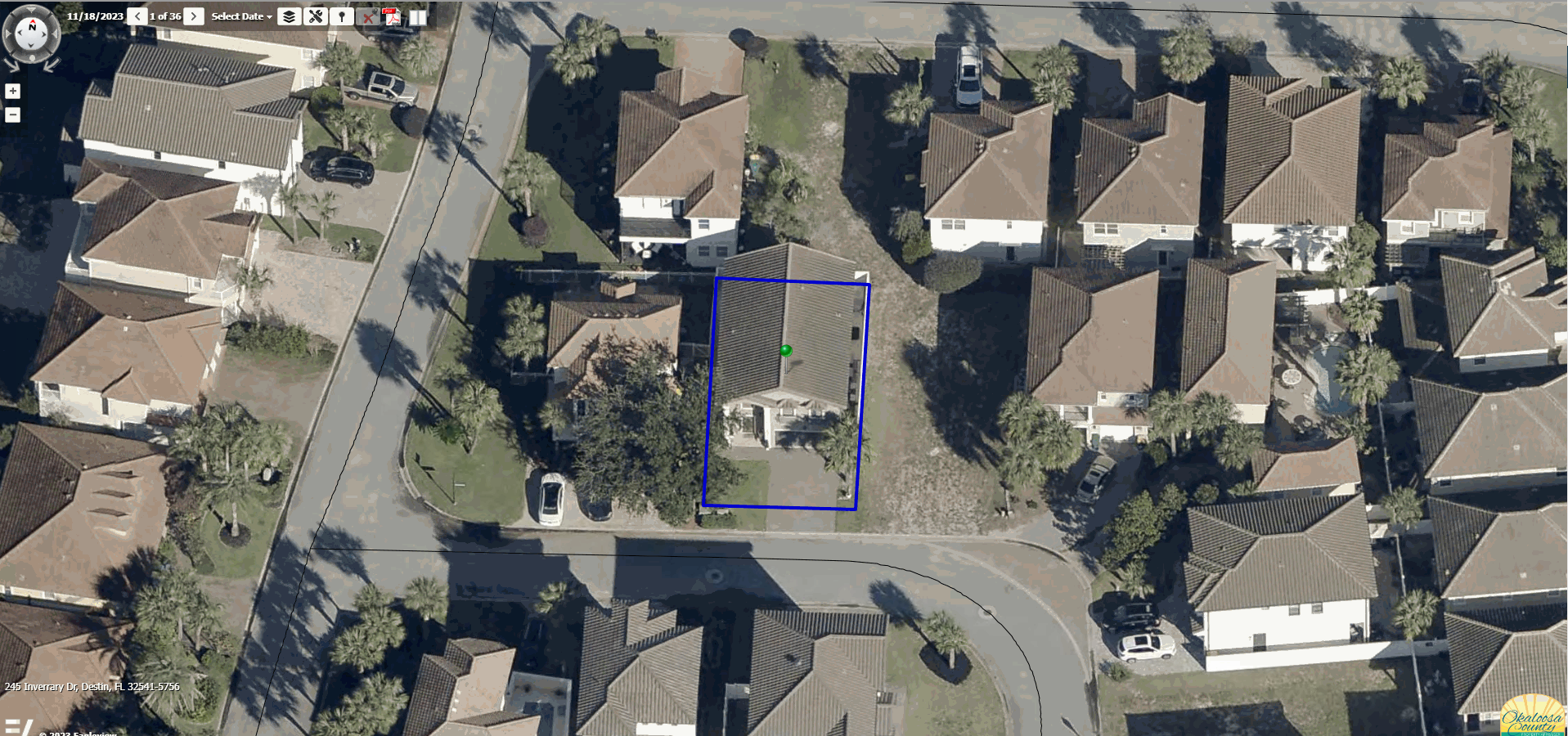
I work in the GIS field for a local government office. We use a piece of software to assess property values, and I was hoping to try to figure out a way to automate the ability to zoom straight to whatever piece of property that our employees are looking at. The only issue with this is our software doesn't house any geographic data, so I couldn't figure out a way to take a property using our identifier number and convert that to latitute and longitude, which I believed was a requirement to utilize the API that our oblique imagery vendor provides.
After some digging and searching the deepest trenches of the web I found someone who was using a method that I didn't know existed. Instead of needing latitude and longitude this person was searching by address! After some tinkering and figuring out exactly what syntax the API needed I was off to the races.
This was a personal victory because I was telling the higher-ups it wasn't a possibility for over a year.
Now I look like a hero!
After some digging and searching the deepest trenches of the web I found someone who was using a method that I didn't know existed. Instead of needing latitude and longitude this person was searching by address! After some tinkering and figuring out exactly what syntax the API needed I was off to the races.
This was a personal victory because I was telling the higher-ups it wasn't a possibility for over a year.
Now I look like a hero!